"Strength of your system is as strong as strength of the weakest link" 😖😓
Microservices expands the attack surface as now - Multiple microservices communicating with each other remotely - Thus instead of one to two endpoints we have 100s of endpoints to worry about.
Thus, with a microservices architecture we need to think better security solution, from multiple perspectives -
- Application Level Security
- Authenticate and Access Control Users
- Secure Communication Channel between Microservices
- Edge Level Security: Using API Gateway Pattern
- Secure Development Life Cycle & Test Automation -
- Speed to production is the key behind Microservices - To ensure engg be able to introduce a change to a microservice, test it and instantly push to production - Proper secure development life cycle is required to not introduce vulnerabilities at code level (Use Static Code Analysis & Vulnerability Testing)
- Proper Test Automation is required to ensure all possible use cases are tested to ensure no regression is injected.
- DevOps Level Security -
- DevOps Security need to concerned about Container Level Security.
- Isolation among Containers
- Isolation between Containers and Host OS.
- Secure communication between Containers and Pods (Kubernetes as Container Orchestration Platform introduced another level of isolation, in the form of 'Pod'.
Well in Microservices world this does not work, as microservices are scoped and deployed in separate containers in a distributed setup. I.e. Interactions are no more local, but remote over Http.
Thus, with a microservices architecture we need to think better security solution.
- JWT (Json Web Token) Based
- TLS - Transport Layer Security
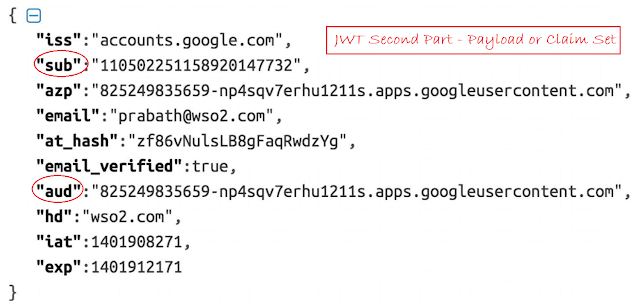
1). JWT: -JWT contains three parts - Header, Payload/Claim Set and Signature. Signature is generated using first two parts.
JWT assert one's identity given that the recipient of the JWT trust the asserting party (token issuer).Issuer of a JWT can sign the payload with a private key to which recipient can validate using the public key.
Note: When issuing a JWT token from a token issues it has to be issued to a given audience. (E.g. Microservice Foo calls Microservice Bar, then the token issuer is Foo and token audience is Bar). The 'aud' parameter in the JWT claim set, represents audience. There can be one or more audience. The value of 'aud' is pre-agreed one between issuer and audience(s).Audience can be generalized using regex like *.facebook.com
In JWT Payload/Claim Set, carries a parameter called 'sub', which represents the subject or the user who owns the JWT. The audience uses this parameter to know the caller.
2). TLS: In Microservices TLS Mutual Authentication is used between microservices to authenticate each other.
B). Edge Security: Using API Gateway:
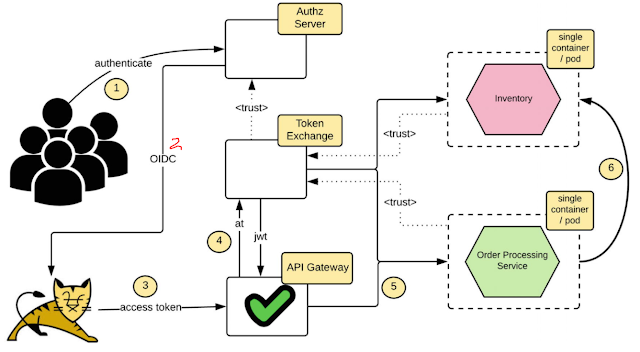
With the API Gateway pattern, Microservices which are exposed outside, should have a corresponding API in API Gateway. Now the end user's access to the microservice (via corresponding API) must be validated at the edge - or the API Gateway.
Most recommended approach is using OAuth 2.0
Here are simple steps:
- Web/Mobile Application user get authenticate using Identity Provider via OpenIDConnect (Or can be SAML 2.0 too)
- Web/Mob app gets an 'access_token', 'refresh_token' and 'id_token'. 'id_token' will identify enduser to Web/Mob app.
- Now Web/Mob app makes an API call - Passing 'access_token'
- API_Gateway reads 'access_token', connect to STS, which will validate 'access_token' and Issue a JWT to the API Gateway. While validating 'access_token' STS will talk to corresponding 'OAuth' Authorization server via an API. This JWT will also carry user context.
- Now the API Gateway will pass thru this JWT while request to downstream microservices.
- Each Microservice will validate the JWT received and then for further downstream calls, it can create a new JWT token (As we discussed in above JWT section) and sends it with request to another microservice.
Note: Responsibility of Authorization Server is:
- Issue tokens ('access_token', 'refresh_token' and 'id_token') to it's clients.
- Also respond to the validation request from downstream services.
- At times plays role of STS too.
There are many open source Authorization Server exists - E.g. WSO2 Identity Server, Keycloak, Gluu etc. Full List of 77 OAuth Providers (Authorization Server) - https://en.wikipedia.org/wiki/List_of_OAuth_providers
Hope this helps...
Arun Manglick







No comments:
Post a Comment